The most common WordPress Security Attacks.
WordPress, the popular open-source Content Management System (CMS), is used by 60% of all websites. However, because it is open-source and can be endlessly customised and optimised, it can be vulnerable to security flaws. According to the Common Vulnerability Score, 8 out of 10 WordPress sites have a medium or high security risk. There are methods to help prevent security attacks, but the key is to first understand the most common security threats to your WordPress sites and then learn how to keep them at bay! This blog provides you with an overview of the most common WordPress security attacks.
Security Attack #1: Brute-force
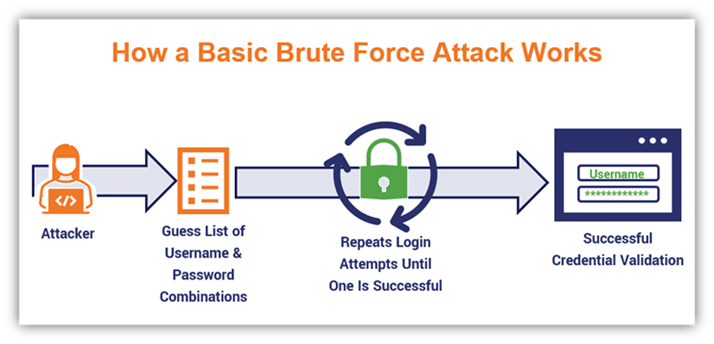
A brute force attack is a popular cracking method, where bad actors attempt to guess login information by using automated password generators.
Types of Brute Force Attacks
- Simple brute force attack—uses a systematic approach to ‘guess’ that doesn’t rely on outside logic.
- Hybrid brute force attacks—starts from external logic to determine which password variation may be most likely to succeed, and then continues with the simple approach to try many possible variations.
- Dictionary attacks—guesses usernames or passwords using a dictionary of possible strings or phrases.
- Rainbow table attacks—a rainbow table is a precomputed table for reversing cryptographic hash functions. It can be used to guess a function up to a certain length consisting of a limited set of characters.
- Reverse brute force attack—uses a common password or collection of passwords against many possible usernames. Targets a network of users for which the attackers have previously obtained data.
- Credential stuffing—uses previously-known password-username pairs, trying them against multiple websites. Exploits the fact that many users have the same username and password across different systems.
Basic Solution: Use strong passwords. For recommendations about how to generate strong passwords, see our Knowledge Base article.
How to Prevent Brute Force Password Hacking
To protect your organization from brute-force password hacking, enforce the use of strong passwords. Passwords should:
- Never use information that can be found online (like names of family members).
- Have as many characters as possible.
- Combine letters, numbers, and symbols.
- Be different for each user account.
- Avoid common patterns.
Why we use Imunify360
Imunify360 is designed to detect abnormal user behaviour including brute-force attacks which are becoming increasingly common with WordPress sites. includes an advanced firewall that uses cloud heuristics and artificial intelligence (AI) to detect threats and block brute-force attacks.
Check out our comparison of Imunify360 and Bitninja
Security Attack #2: Cross-Site Scripting (XSS)
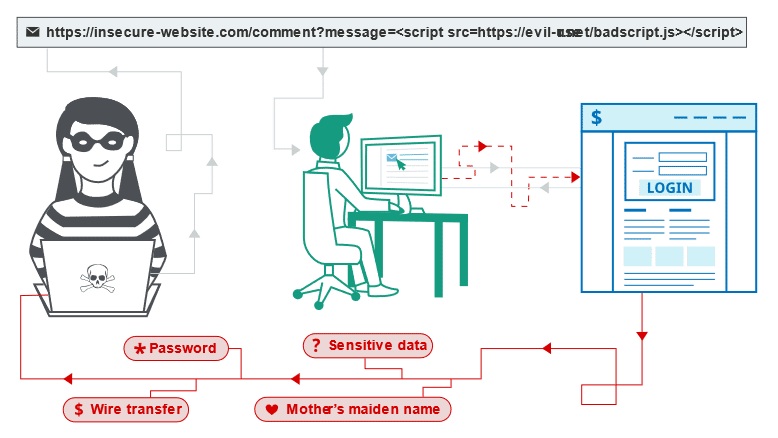
This is a hacking technique where malicious code from user input is injected into web pages and then viewed by site visitors. XSS attacks can potentially extract sensitive information, affect website functionality, and more. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it.
What are the types of XSS attacks?
There are three main types of XSS attacks. These are:
- Reflected XSS, where the malicious script comes from the current HTTP request.
- Stored XSS, where the malicious script comes from the website’s database.
- DOM-based XSS, where the vulnerability exists in client-side code rather than server-side code.
How to prevent XSS attacks
Basic Solution: Wherever a web site receives user input, the input should be filtered as strictly as possible based on the expected or valid input.
Preventing cross-site scripting is trivial in some cases but can be much harder depending on the complexity of the application and the ways it handles user-controllable data.
In general, effectively preventing XSS vulnerabilities is likely to involve a combination of the following measures:
- Filter input on arrival. At the point where user input is received, filter as strictly as possible based on what is expected or valid input.
- Encode data on output. At the point where user-controllable data is output in HTTP responses, encode the output to prevent it from being interpreted as active content. Depending on the output context, this might require applying combinations of HTML, URL, JavaScript, and CSS encoding.
- Use appropriate response headers. To prevent XSS in HTTP responses that aren’t intended to contain any HTML or JavaScript, you can use the Content-Type and X-Content-Type-Options headers to ensure that browsers interpret the responses in the way you intend.
- Content Security Policy. As a last line of defense, you can use Content Security Policy (CSP) to reduce the severity of any XSS vulnerabilities that still occur.
Why we use Imunify360
Using Imunify360 over the default ModSecurity rulesets has several benefits. The first one is that Imunify360 uses heuristic data to detect and stop attacks. This means that the tool takes past information and applies it to the way it detects ongoing attacks. Attackers are forced to continually change their methods of attack and come up with new zero-day exploits. However, the second advantage to Imunify360 is in the way it can detect zero-day attacks based on heuristic data.
Check out our comparison of Imunify360 and Bitninja
Security Attack #3: SQL injection
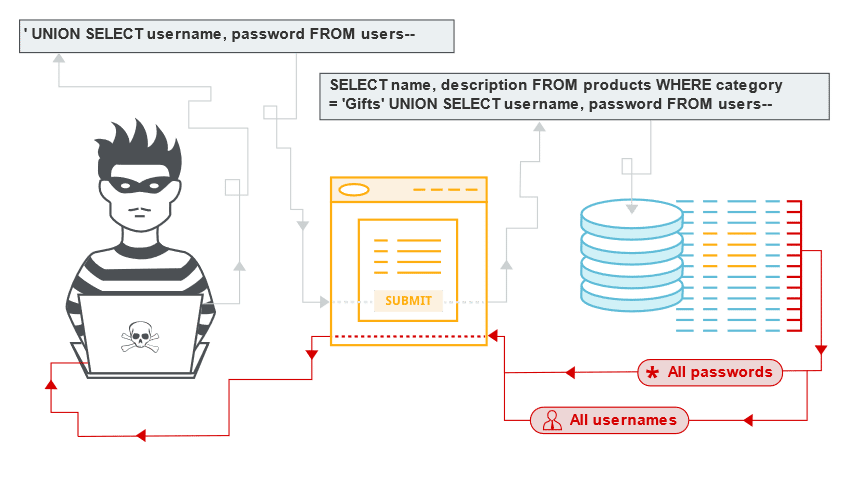
In this type of attack, malicious SQL statements are injected via unsanitized user input. SQL injection attacks can be used to tamper with data, extract sensitive information, and more.
SQL injection examples
There are a wide variety of SQL injection vulnerabilities, attacks, and techniques, which arise in different situations. Some common SQL injection examples include:
- Retrieving hidden data, where you can modify an SQL query to return additional results.
- Subverting application logic, where you can change a query to interfere with the application’s logic.
- UNION attacks, where you can retrieve data from different database tables.
- Examining the database, where you can extract information about the version and structure of the database.
- Blind SQL injection, where the results of a query you control are not returned in the application’s responses.
How to Prevent SQL Injection Attacks?
Basic Solution: Scan your site for SQL injection vulnerabilities using online website scanning tools like Imunify360 or Bitninja.
Preventing or mitigating SQL injection attacks is a lot about ensuring that none of the fields are vulnerable to invalid inputs and application execution. yours is manually impossible to actually to check every page and every application on the website, especially when updates are frequent, and user-friendliness is the top priority. Nonetheless, security analysts and seasoned developers recommend a number of the subsequent points guarantee your database square measure well protected inside the confinement of the server.
- Continuous Scanning and Penetration Testing. The automated web application scanner has been the best choice to point out vulnerabilities within the web applications for quite some time now. Now, with SQL injections getting smarter in exploiting logical flaws, website security professionals should explore manual testing with the help of a security vendor.
They can authenticate user inputs against a set of rules for syntax, type, and length. It helps to audit application vulnerabilities discreetly so that you can patch the code before hackers exploit it to their advantage.
- Restrict Privileges – It is more of a database management function, but enforcing specific privileges to specific accounts helps prevent blind SQL injection attacks. Begin with no privileges account and move on to ‘read-only’, ‘edit’, ‘delete’ and similar privilege levels.
Minimizing privileges to the application will ensure that the attacker, who gets into the database through the application, cannot make unauthorized use of specific data.
- Use Query Parameters – Dynamic queries create a lot of troubles for security professionals. They have to deal with variable vulnerabilities in each application, which only gets graver with updates and changes. It is recommended that you prepare parameterized queries.
These queries are simple, easy to write, and only pass when each parameter in SQL code is clearly defined. This way, your info is supplied with weapons to differentiate between code and information inputs.
- Instant Protection – A majority of organizations fail the problems like outdated code, scarcity of resources to test and make changes, no knowledge of application security, and frequent updates in the application. For these, web application protection is the best solution.
A managed web application firewall can be deployed for immediate mitigation of such attacks. It contains custom policies to block any suspicious input and deny information breach instantly. This way, you do not have to manually look for loopholes and mend problems afterward.
Why we use Imunify360
Imunify360 will help you be proactive and stop exploits, injected pharma links, hacked content, conditional redirects from XSS, and many other web-related threats that harm websites and damage reputation.
Check out our comparison of Imunify360 and Bitninja
Security Attack #4: Backdoor
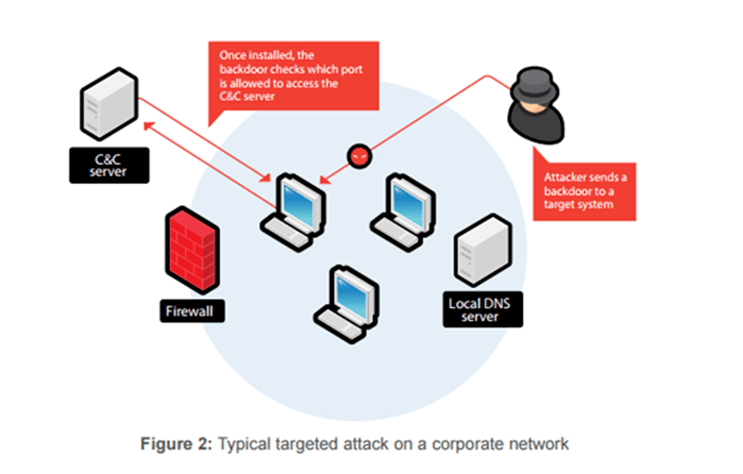
A backdoor is malicious code that contains a hidden way to bypass the login or authentication process of a website.
Types of Backdoor Attack:
There are two different types of Backdoor attacks. They are as listed as follows –
1. Administrative Backdoor Attack: Sometimes software developers purposefully leave a backdoor in the program so that if there is a failure or error, they can easily access the core of the software’s code and immediately resolve the problem. Administrative Backdoors are the name given to such Backdoors. These intentional Backdoors can also assist software testers in validating the codes.
Although these Backdoors are only known to developers, a skilled hacker can exploit them and use them invisibly to his advantage. As a result, Administrative Backdoor can be considered a type of program loophole.
2. Malicious Backdoor Attack: A malicious Backdoor Attack occurs when the program gets into the system through harmful malware.RAT (Remote Access Trojan) is used by cyber attackers for installing malicious backdoor programs.
Prevention of Backdoor Attack:
Basic defense: Make sure your server has antivirus and firewall protection and is kept up to date. Also make sure you keep WordPress itself and any associated plugins updated with the latest security patches.
Prevention is better than cure. Listed are some ways to prevent Backdoor attacks from taking place:
- Continuous Monitoring of Security System: Monitoring the system network helps in checking loopholes that may turn into potential entry points for backdoor attacks.
- Having Strong firewalls in Computer Network: Firewall filters the traffic in a computer network and a strong firewall can prevent attackers from getting into the system.
- Protection of computer networks through Strong Passwords: Having a strong password helps in establishing the strong security of the system. Users should never stick to default passwords and should always have passwords that are difficult to guess or crack.
- Stop accessing unauthorized and unverified websites/content over the internet. Especially, one should take extra precautions while accessing free websites/software. Such places are a hub for viruses and ill-intended content and can cause serious damage to your system.
- Update your OS and software at-service as updated resources can fight the attack attempts in a better way.
- With the help of a firewall, things could be way better than earlier as this piece of technology will keep an eye on all the incoming and outgoing traffic and take immediate action when anything suspicious is noticed.
- An anti-malware program is useful to keep malicious content at bay. It will automatically detect and eliminate dangers like viruses, malware, Trojans, and so on and keep the system protected. As everything happens automatically, not much effort is required.
Why we use Imunify360
Imunify360 is a completely automated tool that monitors and protects CMS-based sites out-of-the-box. After it’s deployed to a server, administrators can rely on virtual patching to secure outdated applications and keep users’ files consistent.
Outdated WordPress sites are another severe vulnerability. Site owners might not be fully aware of the danger of leaving WordPress and its plugins unpatched. Imunify360 takes care of this issue by doing a virtual patching and leaving WordPress site intact to ensure the secure version of the code is always running on all hosted websites.
Check out our comparison of Imunify360 and Bitninja
Security Attack #5: Denial-of-Service (DoS) attacks
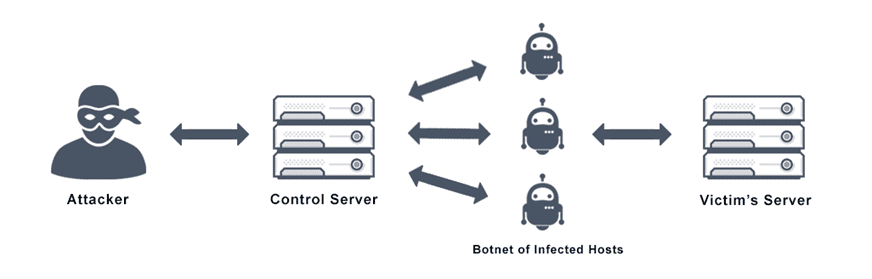
This type of attack renders a website inaccessible or unavailable to its users. For example, a Distributed Denial-of-Service (DDoS) attack sends traffic from multiple sources to a website, overwhelming its network connection.
Types of DoS Attacks
There are generally two types of DoS attacks we need to be prepared for: volume-based and logic-based.
- Volume-based Attacks. This type of DoS is the one most are familiar with. In a volume-based attack, the attacker simply attempts to flood a service or connection with so much traffic that communications either become unusably slow, or the service crashes altogether.
- Logic-Based Attacks. In a logic-based attack, the attacker attempts to exploit a flaw in a service to take it offline. For example, if an attacker finds a vulnerability in an unpatched web server, and uses that vulnerability to degrade the performance of the server, that would be a logic-based attack. It didn’t take a lot of resources; it only took a “logic” flaw to degrade service.
You may have also heard of a “Distributed Denial of Service” attack – or DDoS. A DDoS attack is usually a volume-based attack that uses a network of computers to attack a single source. The attacks are most often conducted using machines that don’t belong to the attacker (previously compromised) and can be both highly effective and highly challenging to stop.
How To Prevent Denial-of-Service (DoS) Attacks
Basic Solution: Using a well-established Content Delivery Network (CDN) such as Cloudflare can help mitigate or even prevent these types of attacks.
Denial of Service attacks can be tricky to defend against. Organizations can take the following actions toward denial-of-service attack protection and prevention:
- Monitor and analyse network traffic: Network traffic can be supervised via a firewall or intrusion detection system. Administrators can set up rules that create alerts for unusual traffic, identify traffic sources or drop network packets that meet a certain criteria.
- Strengthen their security posture: This includes fortifying all internet-facing devices to prevent compromise, installing, and maintaining antivirus software, establishing firewalls configured to protect against DoS attacks and following robust security practices to monitor and manage unwanted traffic.
- Monitor traffic: Organizations can enrol in a service that detects or redirects the abnormal traffic flows typically associated with a DoS attack, while allowing normal traffic to proceed on the network.
- Establish a DoS attack response plan: The key is to create and practice a disaster recovery plan for DoS attack that covers communication, mitigation and recovery.
Why we use Imunify360
Imunify360 takes care of several sophisticated attacks that create excessive CPU usage. It will stop denial-of-service, and the botted traffic that could cause performance degradation on your server. The results will let host providers keep full control of their server’s CPU usage and reduce support ticks, increase profitability, and maintain customer satisfaction. It reduces server load caused by DoS and brute-force attacks and malware running on infected sites. It eliminates the resources used by malware and returns it to the users that need it.
Check out our comparison of Imunify360 and Bitninja
Security Attack #6: Phishing
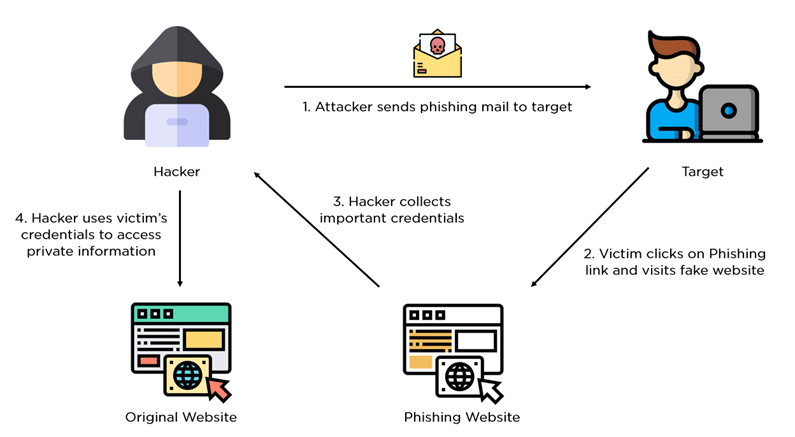
Attackers use the phishing technique to impersonate a legitimate company, typically via email, in order to obtain personal information directly from the target. The attacker then uses the information to hack the site or commit fraud.
In a typical phishing attack, scammers send fake emails to thousands of people, asking for sensitive information (such as bank details), or containing links to bad websites. They might try to trick you into sending money, steal your details to sell on, or they may have political or ideological motives for accessing your organisation’s information. Phishing emails are getting harder to spot, and some will still get past even the most observant users. Whatever your business, however big or small it is, you will receive phishing attacks at some point.
Types of Phishing Attacks
- Email phishing scams: Fraudulent messages sent out to random users in bulk through email.
- Spear phishing: Highly targeted type of phishing, attacking specific users.
- Whaling: Big fish such as CEOs or other high-level executives are targeted based on in-depth profiling.
- Smishing: Fraudulent SMS alerts in this phishing attack
- Vishing: Phishing orchestrated using phone calls or other voice-based media.
- Pharming: The victims are redirected to fraudulent websites using DNS cache poisoning.
- Social media phishing: Social media platforms are used for this attack type.
How To Prevent phishing attacks:
Basic Solution: Spam filters can detect and prevent most malicious emails from reaching users’ inboxes.
- Educate your employees and conduct training sessions with mock phishing scenarios.
- Deploy a SPAM filter that detects viruses, blank senders, etc.
- Keep all systems current with the latest security patches and updates.
- Install an antivirus solution, schedule signature updates, and monitor the antivirus status on all equipment.
- Develop a security policy that includes but isn’t limited to password expiration and complexity.
- Deploy a web filter to block malicious websites.
- Encrypt all sensitive company information.
- Convert HTML email into text only email messages or disable HTML email messages.
- Require encryption for employees that are telecommuting.
There are multiple steps a company can take to protect against phishing. They must keep a pulse on the current phishing strategies and confirm their security policies and solutions can eliminate threats as they evolve. It is equally as important to make sure that their employees understand the types of attacks they may face, the risks, and how to address them. Informed employees and properly secured systems are key when protecting your company from phishing attacks.
Why we use Imunify360
Imunify360, uses a URL scanner to check incoming links, a link sanitizer that clears out dangerous links, an email scanner that blocks spoofed emails and an email whitelisting feature.
Check out our comparison of Imunify360 and Bitninja
Security Attack #7: Hotlinking
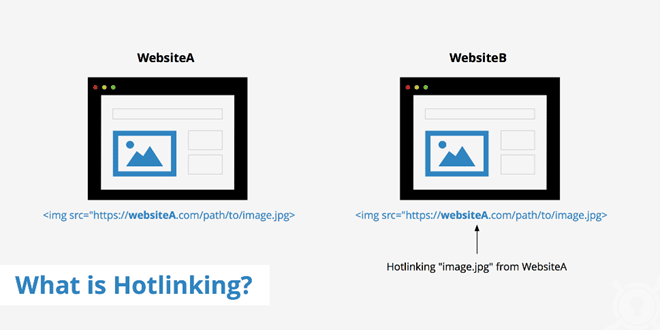
This is a technique where a website links directly to the targeted website’s assets, such as video or image files, in order to increase SEO ranking or to feature media without using their own server resources or bandwidth. For example, if website B hotlinks to website A’s featured image, and website B receives a lot of traffic on the page with the image, website A’s server resources are depleted, potentially affecting website A’s performance.
How to Prevent Hotlinking
Basic Solution: Use a plugin or Content Delivery Network (CDN) such as Cloudflare to help protect your media files.
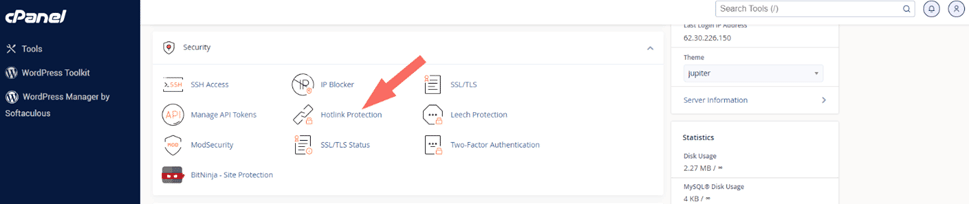
Using cPanel – Hotlink Protection Option
If you use cPanel, you can find the Hotlink Protection feature in its Security section. Open and configure it to utilize the facility.
To block direct access to files of specific types, add those file extensions to the Block direct access for the following extensions text box. For example, to block all .jpg images, you would add .jpg to the Block direct access for the following extensions text box.
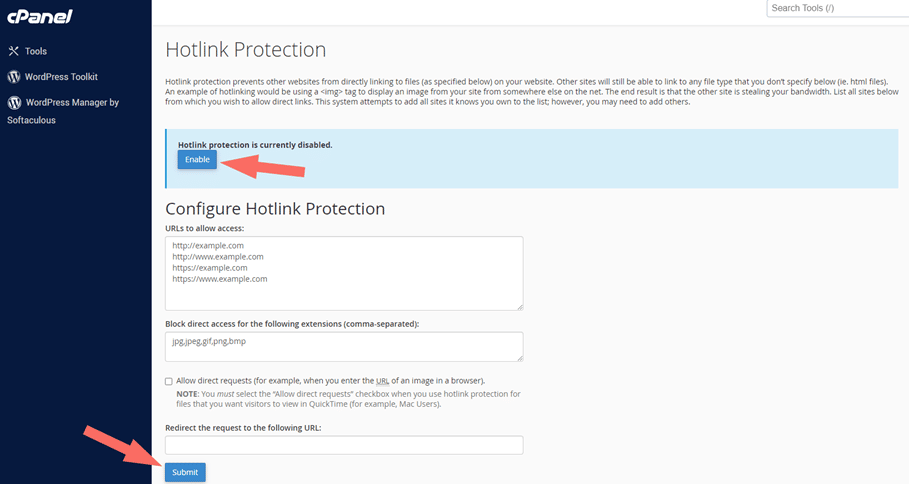
You can configure Hotlink Protection to give access to the URLs you want. Those URLs can link to your files directly. Additionally, you may redirect all requests that will be blocked to a specific URL, for example, with a warning image.
Other ways to prevent hotlinking.
1. Use a CDN with hotlink protection
Use a CDN with built-in hotlink protection. CDN providers like Cloudflare already have built-in free hotlink protection. This feature will block direct website links to your graphic resources. However, visitors can still view and download images from your website. This means they can properly download, post, and cite images from your site.
2. Disable right click functionality
To hotlink an image, users can right-click the image, copy the image’s address, and paste the URL into their site. So it makes sense to disable the right click feature. This can help you reduce the total number of image copies on your site. For WordPress websites, you can use, for example, the out-of-the-box Content Theft Prevention plugin. This plugin not only disables right-clicking on your images, but on the entire page, thus protecting your content.
Add a watermark to your images – A more convenient solution is to add a watermark to your images and other media objects. This solution won’t stop every user from hotlinking your resources, but it will make some think twice. While your website will most likely include a copyright notice in your website footer, you can highlight your ownership of your content by adding a text watermark to all of your images (or your most popular ones). This watermark can simply include your name, copyright logo or trademark.
Rename hotlinked files – If you notice that a single image is being referenced by a high traffic website or multiple websites causing a spike in bandwidth usage, you can rename the file. By changing the URL of an image on your website, you will break hot links, resulting in a 404 error. This solution is not easy to scale, but it is effective for quick fixes.
Issue a takedown request – A more direct approach to responding to websites that have links to resources on your site is to submit a takedown request. A Digital Millennium Copyright Act (DMCA) notice informs a company, web host, search engine, or ISP that they host or link to infringing material. DMCA notices are a valuable tool for writers, photographers, videographers, and anyone whose content may be infringed online. You can submit the DMCA notice yourself or hire an agent to do it for you.
Why Brixly recommends Imunify360
At Brixly we use Imunify360 to protect ourselves and our users from various online attacks. These attacts range from brute-force, Cross-Site Scripting, SQL injection, Hotlinking, Backdoor, Phishing and Denial-of-Service attacks
Imunify360 uses a multi-layer approach to provide protection against malicious attacks and abnormal behaviour, including distributed brute-force attacks. Imunify360 offers advanced firewall protection that uses cloud heuristics and artificial intelligence to detect new threats and protect servers.
Whether it’s PHP vulnerabilities, poorly coded plugins, malware, or brute-force attacks, Imunify360 provides all-level enterprise protection. It scans your system for malware, blocks ongoing brute-force attacks, and cleans up injections from your code. With Imunify360, you can proactively protect your applications from sophisticated attacks that would otherwise silently compromise your system, inject malicious code, and potentially exfiltrate data for months.
Check out our comparison of Imunify360 and Bitninja
Finishing off…
Website security is an essential part of running a business online. It protects against threats like malware and phishing attacks. With Imunify360, you can defend your website against these dangers. This software has a real-time malware scanner, URL scanner, and link sanitizer. It also scans emails for malware and has an email whitelisting feature. These features help you stay secure and keep your site safe from harm. With Imunify360, you can defend your business against cyber attacks and keep your site safe for visitors.
In addition, its crucial that you keep your local machine clean of viruses and malware to prevent any exploits from being uploaded to your services via FTP or the clean files on your machine becoming infected. As such, we would always encourage you to install an antivirus solution for Windows or Mac devices, schedule signature updates, and monitor the antivirus status on your equipment.
Now that you understand the various types of security threats to be aware of, consider the following root causes of why your WordPress site may be vulnerable to security breaches:
- Your WordPress site is out of date and requires an update to the most recent version.
- You have unused or outdated themes or plugins installed on your site, which cause compatibility issues and open up security holes.
- Your WordPress site admin login page is still set to the default /wp-admin, making it vulnerable to brute-force attacks.
- Give your site a thorough security audit, or contact the Brixly team if you need help to improve the security of your WordPress sites.
After auditing and updating your website you should make sure all the steps above are monitored at all times.


